
Articles
Features
Articles
Controls & Automation
Safety
Software
Two fundamental principles will help you make great industrial cybersecurity decisions
July 20, 2022 | By Felipe Sabino Costa
On the plant floor, this responsibility is increasingly falling to the in-house electrician who must specify, install and maintain the sensors, actuators, and other communications devices.
 Autonomous underwater vehicle (AUV) rover-drone inspecting a submarine internet communication cable on the seabed (illustration). Photo: Jesper / Adobe Stock
Autonomous underwater vehicle (AUV) rover-drone inspecting a submarine internet communication cable on the seabed (illustration). Photo: Jesper / Adobe Stock July 20, 2022 – To accelerate their digitalization journeys, manufacturers are implementing innovative networking technologies to capture, transmit and, ultimately, transform industrial data into meaningful insights.
Unfortunately, all this connected equipment poses new cybersecurity risks to industrial control systems and, therefore, requires security features at the component level to mitigate these risks.
On the plant floor, this responsibility is increasingly falling to the in-house electrician who must specify, install and maintain the sensors, actuators, and other communications devices that enable machines to talk to each other.
How did we get here?
Until the 1990s, manufacturing largely occupied two separate universes: Information Technology (IT) and Operational Technology (OT). The OT universe was composed of heavy machinery, electrical devices, processing systems, and other industrial equipment. Born out of the information age, the IT universe relies on servers, storage, networking and PCs running applications and processing data.
Like two ships passing in the night, IT and OT occupied separate silos, shared little data or control, and relied on oversight from staff with divergent skill sets and agendas.
With the advent of the Industrial Internet of Things (IIoT), these two worlds have converged, resulting in productivity gains on a scale never seen before. Data gathered from sensors and actuators throughout a plant collect equipment and environment data for analysis, leading to improved decision-making and employee safety, streamlined supply chains, cost-saving predictive maintenance, and reduced waste.
Amidst all this excitement, however, an old problem has grown into a new danger posing far higher stakes: cyberattacks.
With all its connectivity and devices, the IIoT makes an appealing target for hackers. The expanded attack surface gives bad actors the opportunity to move laterally across a network, jumping across IT and OT systems to conduct industrial espionage, intellectual property theft, or even production sabotage.
Any point in an IIoT infrastructure that a hacker can use to gain unauthorized access is an attack vector, and this includes devices, software, machines, input touchpoints, displays, sensors—even people. Hackers only need identify the weakest link in the system.
In this article, I will introduce specific action items based on well-defined frameworks and standards when building a cybersecurity management system (CSMS) for your own industrial control system (ICS). Taking a defence-in-depth approach to network construction and choosing secure-by-design solutions from trusted vendors can help simplify the ICS cybersecurity decision-making process.
Key elements of the cybersecurity management system
To understand the key elements of the CSMS, let’s take an in-depth look at the ISA/IEC 62443 series of standards, which provide a holistic and wide-ranging approach to securing ICSs. These standards are holistic because they embrace the different structural aspects of security strategy, defined by the International Electrotechnical Commission (IEC) as People, Processes, and Technologies.
In addition, these standards cover a lot of ground because they provide internal and external recommendations to asset owners, supply chain management, and product development teams.
Although the IEC 62443 series provides a wealth of information in an ever-expanding spectrum of field applications, it can be difficult to distil concrete action items for building your own industrial control system’s CSMS. So I will identify the main elements in the CSMS development process proposed by the IEC 62443 series.
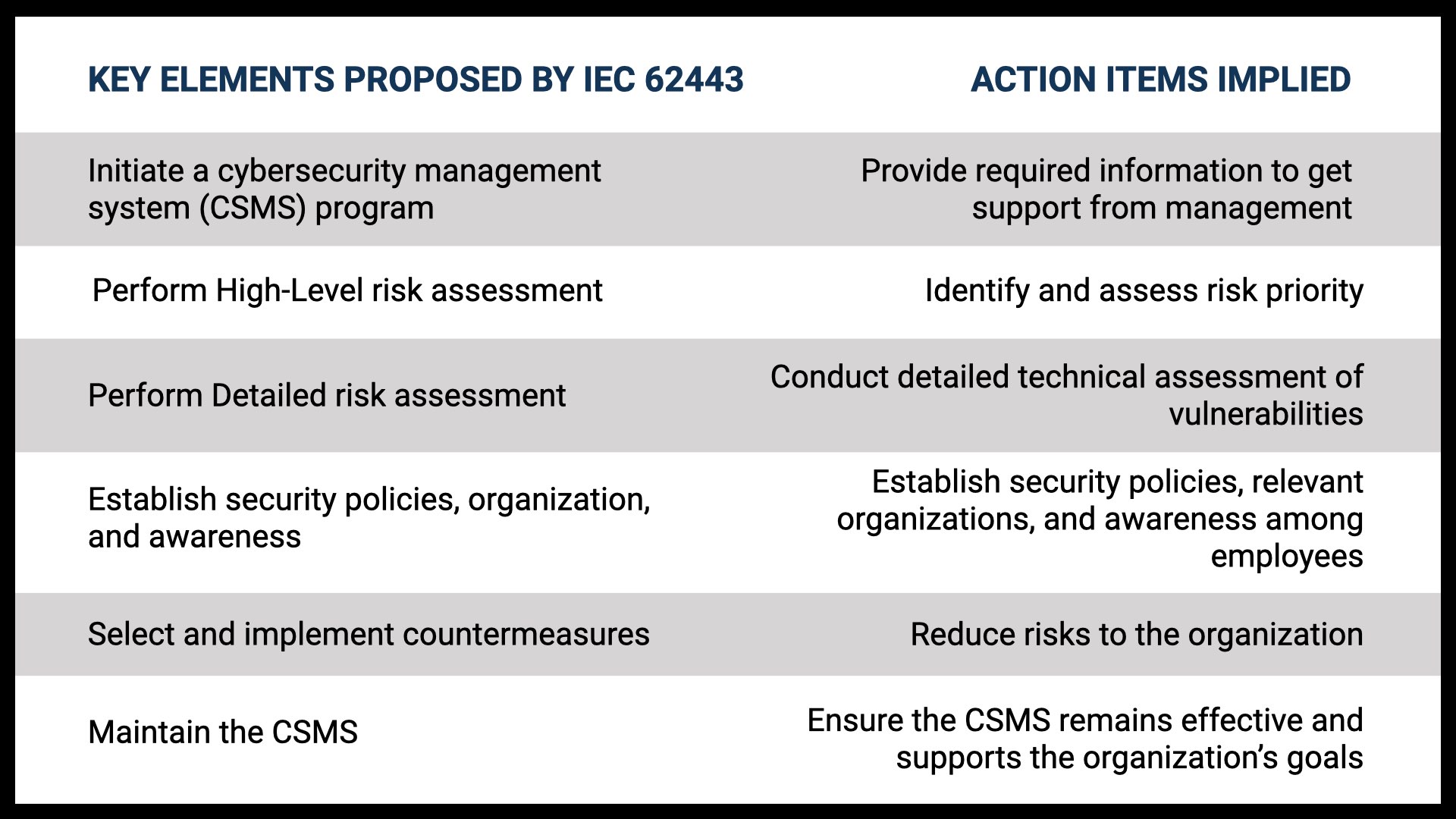
Open image in new tab or window to see full size version
Asset owners, system integrators, and product suppliers play key roles in the whole cybersecurity management system as suggested in ISA/IEC 62443 (see Chart 1). In particular, IEC 62443 recommends that asset owners analyze, address, monitor, and improve the CSMS’s ability to defend itself against risks in accordance with the company’s risk appetite. In addition, IEC 62443 recommends security development throughout the product life cycle so as to maintain an acceptable level of security in the products and systems the solution providers or system integrators offer.
Two fundamental principles from the IEC framework encourage you to take the following concrete actions:
1. Take a defence-in-depth approach to network construction.
2. Choose vendors that provide secure-by-design solutions, which includes after-sales service and established security response processes.
Following these two principles will help you protect your devices from security vulnerabilities and help you to manage security risks better.
Risk assessment
Risk assessment is an important aspect of every company’s overall risk management strategy, and is mandatory for creating a solid cybersecurity strategy. It requires correlation and collaboration between many different groups of people within the company.
These levels have been defined by the National Institute of Standards and Technology (NIST) as the Organization, Mission/Business Processes, and Information System (IT and ICS) levels. Risk management aims to assess and understand the different types of risks to which the company is susceptible, in areas such as investment, budgeting, legal liability, safety, inventory, and supply chain. The industrial control system often considered to be one of the greatest potential areas of risk for an organization.
To perform a risk assessment of the ICS, it is necessary to define the scope and boundaries of the system that will be assessed (a.k.a. the “System under Consideration”, or SuC). Once the SuC is defined, it is necessary to systematically identify and analyze the threats and vulnerabilities, and prioritize the risks based on their potential consequences. At the same time, it is also important to define asset criticality and dependencies to the operation.
The risk formula is as follows:
Likelihood (Event Occurring) = Likelihood (Threat Realized) × Likelihood (Vulnerability Exploited)
Risk = Likelihood (Event Occurring) × Consequence
The consequence can be measured in dollars, production downtime, wasted product, network disruption time—anything that would impact operations negatively. Combining likelihood and consequence produces a residual risk rating e.g. Low, Medium, High.
Two different types of risk assessment apply to industrial control systems: High-Level and Detailed. As their names suggest, one approach deals primarily with high-level concepts, while the other involves a detailed look at the different types of risk. It is common to perform a High-Level risk assessment to support the business rationale and business case, then a Detailed assessment to ensure the system has specific countermeasures included in the design.
An expected outcome from this step is a comprehensive list of critical assets and where connectivity occurs between them. The assessment should also identify dependencies (i.e. Task B cannot occur without Task A having been completed first), and determine critical risks to the operation/safety of processes and appropriate responses, which includes partitioning the system into zones and conduits to mitigate risks to acceptable levels.
Build defence-in-depth networks
One of the most common security weaknesses in an industrial control system is the use of flat networks that allow all the devices on a network to communicate with each other, even when it is unnecessary. A flat architecture contributes to a lack of control over information on the network, and facilitates both threat propagation and communication degradation.
Taking a page out of the military playbook, asset owners should adopt the defence-in-depth approach when building their network. In the military context, it refers to implementing multiple layers of protection to prevent an intruder from advancing. Similarly, defence-in-depth networks are partitioned into multiple zones and conduits, which are then assigned different security levels, depending on associated risks.
Assess security levels
An important part of the defence-in-depth strategy is to consider countermeasures for zones and internal products. Accordingly, ISA/IEC 62443 introduces the concept of security levels that can be applied to zones, conduits, channels, and products. The security level (SL) is defined by researching a particular device, then determining the level of security it should have, depending on its place in the system.
There are four (4) distinct security levels (ISA/IEC 62443 also mentions an “open” level—Level 0—but it is rarely used), ranging from Level 1 (casual exposure) to Level 4 (intentional attack with extensive resources).
Once the required SL of a zone is defined, it is necessary to determine whether the devices inside that zone meet the security level. When they do not, it is necessary to consider countermeasures that can help reach the required security level. They may be technical (e.g. firewall), administrative (e.g. policy), or physical (e.g. locked door).
Not every zone, conduit, or device requires Level 4 security. Asset owners or system integrators need to conduct a detailed risk analysis to determine the appropriate level of risk for each zone and conduit in their system. In other words, there is an inherent balancing of risk and cost to consider.
Choose hardened components
The concept of security levels also applies to the components that go into building the system. In fact, IEC 62443-4-2 specifically defines the security requirements for four types of components:
1. Software applications
2. Embedded devices
3. Host devices
4. Network devices
For each type of component, the standard also defines seven foundational requirements:
1. Identification and authentication control
2. Use control
3. System integrity
4. Data confidentiality
5. Restricted data flow
6. Timely response to events
7. Resource availability
Luckily, several laboratories (such as Bureau Veritas and ISA Secure) can certify products to ensure they adhere to IEC 62443-4-2 requirements. These labs can simplify the selection process for asset owners. All you need to do is determine the level of security required and select a certified product meeting that requirement.
This component-level security assurance, also known as hardening, adds another layer of protection to the system as part of a defence-in-depth strategy.
Select secure-by-design suppliers with after-sales support
Besides selecting security-hardened devices, asset owners also need to pay careful attention to supply chain management practices. In fact, after-sales support and response to vulnerabilities are just as important as how the devices are designed and built. The components that go into building a cybersecurity management system often come from separate vendors; should one vendor’s device become compromised, the remaining devices in your entire system could be, too.
So, besides device-level security, you should choose suppliers that provide security over the entire product life cycle, including support, quality control, validation of performance, and vulnerability responses, among others.
In other words, the product’s entire life cycle needs to be secure-by-design. IEC 62443 even has a dedicated subsection (62443-4-1) specifying the requirements for ensuring “secure-by-design” throughout the product life cycle (building, maintaining, discontinuing). These requirements are generally associated with the support needed for patch management, policies, procedures, and security communications about known vulnerabilities.
Similar to the IEC standard for product certification, a solutions provider can be certified as following good security management practices, and adhering to tangible criteria in IEC 62443-4-1. This simplifies the asset owner’s decision-making process.
Moreover, selecting a trusted vendor that takes a proactive approach to protecting their products from security vulnerabilities and helping customers manage those risks through a dedicated response team can also help ensure your supply chain is protected, even as new vulnerabilities and threats emerge.
Follow the principles
Protecting the industrial control systems that keep critical infrastructure around the world up and running is a daunting task. Although many guidelines and standards are available for developing a holistic cybersecurity management system for industrial networks, asset owners, system integrators, and product suppliers need to work together when building their own systems and applications.
Adopting a defence-in-depth approach to network construction and selecting secure-by-design suppliers that provide proactive responses to vulnerabilities can help simplify the inherent complexity of building your own cybersecurity management system.
Felipe Sabino Costa is an electrical and electronics engineer and an official ISA/IEC-62443 industrial cybersecurity instructor for the International Society of Automation. He is also a LATAM industrial cybersecurity (IACS) expert, an international speaker, and an author of books and white papers. With over 15 years inside the industrial sector dealing with an array of technologies and products, Felipe is dedicated to developing mission-critical solutions that include cybersecurity by design. Felipe holds cybersecurity certifications from the US Department of Homeland Security, MIT and Stanford, and is working on an M.Sc. in Cybersecurity. He also has a specialization from Harvard University in Innovation and an MBA in Marketing.
You’ll find all Back Issues of Electrical Business Magazine in our Digital Archive.
Print this page
